“Securing your containers, empowering your DevOps.”
Container Security Best Practices for DevOps Teams are essential to ensure the protection of applications and data within containerized environments. As DevOps teams increasingly adopt containerization for their software development and deployment processes, it becomes crucial to implement robust security measures to mitigate potential risks and vulnerabilities. This introduction will provide an overview of the best practices that DevOps teams should follow to enhance container security and safeguard their applications and infrastructure.
Importance of Container Image Scanning in DevOps Container Security
Container Security Best Practices for DevOps Teams
In today’s fast-paced software development landscape, DevOps teams are constantly looking for ways to streamline their processes and improve efficiency. One area that has gained significant attention in recent years is container security. As more and more organizations adopt containerization as a means of deploying applications, it becomes crucial to ensure that these containers are secure and free from vulnerabilities. This article will explore the importance of container image scanning in DevOps container security and provide some best practices for DevOps teams to follow.
Container image scanning is a critical component of container security. When a container is created, it is built from a base image that contains all the necessary dependencies and libraries. However, these base images can often contain vulnerabilities that can be exploited by attackers. By scanning container images for known vulnerabilities, DevOps teams can identify and address these issues before the containers are deployed.
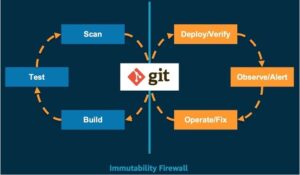
One of the key benefits of container image scanning is that it allows DevOps teams to catch vulnerabilities early in the development process. By integrating image scanning into the CI/CD pipeline, teams can automatically scan container images as they are built. This ensures that any vulnerabilities are identified and addressed before the containers are deployed to production. By catching vulnerabilities early, teams can reduce the risk of security breaches and minimize the impact on their applications and infrastructure.
Another important aspect of container image scanning is the ability to continuously monitor containers for new vulnerabilities. As new vulnerabilities are discovered, security researchers and vendors release updates and patches to address these issues. By regularly scanning container images, DevOps teams can ensure that their containers are always up to date and free from known vulnerabilities. This proactive approach to security helps to minimize the risk of attacks and ensures that applications are running on secure and reliable infrastructure.
To effectively implement container image scanning, DevOps teams should follow some best practices. Firstly, it is important to choose a reliable and reputable image scanning tool. There are several commercial and open-source tools available that can help teams scan container images for vulnerabilities. It is crucial to select a tool that provides accurate and up-to-date vulnerability information and integrates seamlessly into the CI/CD pipeline.
Additionally, teams should establish a regular scanning cadence to ensure that containers are continuously monitored for vulnerabilities. This can be done by scheduling regular scans or by integrating scanning into the build and deployment process. By establishing a regular scanning cadence, teams can ensure that any new vulnerabilities are quickly identified and addressed.
Furthermore, it is essential to establish a process for addressing vulnerabilities that are discovered during scanning. This process should include clear guidelines on how to prioritize and remediate vulnerabilities based on their severity. By having a well-defined process in place, teams can efficiently address vulnerabilities and minimize the impact on their applications and infrastructure.
In conclusion, container image scanning is a crucial aspect of container security for DevOps teams. By scanning container images for vulnerabilities, teams can catch issues early in the development process and continuously monitor containers for new vulnerabilities. By following best practices such as choosing a reliable scanning tool, establishing a regular scanning cadence, and implementing a process for addressing vulnerabilities, DevOps teams can ensure that their containers are secure and free from known vulnerabilities. By prioritizing container security, organizations can minimize the risk of security breaches and ensure the reliability and integrity of their applications.
Implementing Access Controls and Privilege Management for Container Security in DevOps
Implementing Access Controls and Privilege Management for Container Security in DevOps
Containerization has revolutionized the way software is developed and deployed, enabling DevOps teams to build and ship applications faster than ever before. However, with this increased speed and agility comes the need for robust security measures to protect sensitive data and prevent unauthorized access. In this article, we will explore some best practices for implementing access controls and privilege management in container security for DevOps teams.
Access controls are a fundamental aspect of any security strategy, and container environments are no exception. One of the first steps in securing your containers is to ensure that only authorized individuals have access to them. This can be achieved by implementing strong authentication mechanisms, such as multi-factor authentication, to verify the identity of users before granting them access.
Furthermore, it is crucial to establish role-based access controls (RBAC) to define and enforce the level of access each user or group of users has within the container environment. RBAC allows you to assign specific privileges and permissions based on job responsibilities, ensuring that only those who need access to certain resources can interact with them. Regularly reviewing and updating these access controls is essential to maintain the integrity of your container security.
Privilege management is another critical aspect of container security. By default, containers run with elevated privileges, which can pose a significant risk if not properly managed. DevOps teams should adopt the principle of least privilege, granting containers only the permissions they need to perform their intended functions. This reduces the attack surface and minimizes the potential impact of a security breach.
To implement privilege management effectively, it is recommended to use container orchestration platforms that offer built-in security features. These platforms allow you to define and enforce security policies at the container level, ensuring that containers are isolated from each other and have limited access to the underlying host system. Additionally, regularly scanning container images for vulnerabilities and applying patches promptly is crucial to mitigate potential security risks.
In addition to access controls and privilege management, monitoring and logging play a vital role in container security. DevOps teams should implement robust monitoring solutions that provide real-time visibility into container activities, allowing them to detect and respond to security incidents promptly. This includes monitoring for unauthorized access attempts, abnormal behavior, and potential security vulnerabilities.
Logging is equally important for container security. By capturing and analyzing logs generated by containers, you can gain valuable insights into the security posture of your environment. This includes tracking user activities, identifying potential security breaches, and conducting forensic investigations if necessary. Implementing a centralized logging solution that aggregates logs from all containers simplifies the monitoring and analysis process, enabling you to identify and respond to security incidents effectively.
Lastly, regular security assessments and audits are essential to ensure the effectiveness of your container security measures. Conducting vulnerability assessments and penetration testing helps identify potential weaknesses in your container environment, allowing you to address them before they can be exploited. Additionally, performing regular audits of access controls, privilege management, and monitoring processes helps ensure compliance with industry regulations and best practices.
In conclusion, implementing access controls and privilege management is crucial for container security in DevOps teams. By establishing strong authentication mechanisms, role-based access controls, and least privilege principles, you can protect sensitive data and prevent unauthorized access. Additionally, monitoring, logging, and regular security assessments help maintain the integrity of your container environment. By following these best practices, DevOps teams can ensure that their containerized applications are secure and resilient in today’s rapidly evolving threat landscape.
Best Practices for Securing Container Orchestration Platforms in DevOps
Container Security Best Practices for DevOps Teams
In today’s fast-paced software development landscape, DevOps teams are increasingly adopting containerization as a means to streamline their processes and improve efficiency. Containers offer a lightweight and portable solution for packaging applications and their dependencies, allowing for easy deployment across different environments. However, with the rise of containerization, security concerns have also become a top priority for DevOps teams. In this article, we will explore some best practices for securing container orchestration platforms in DevOps.
One of the first steps in ensuring container security is to use trusted container images. It is crucial to only use images from reputable sources, as malicious or compromised images can introduce vulnerabilities into your environment. Additionally, regularly updating and patching container images is essential to address any known security vulnerabilities. By keeping your container images up to date, you can minimize the risk of exploitation.
Another important aspect of container security is implementing strong access controls. DevOps teams should enforce strict access controls to limit who can interact with container orchestration platforms. This includes using strong authentication mechanisms, such as multi-factor authentication, and regularly reviewing and revoking unnecessary privileges. By implementing these access controls, you can reduce the risk of unauthorized access and potential attacks.
Furthermore, it is crucial to monitor container activity and implement logging and auditing mechanisms. By monitoring container activity, you can detect any suspicious behavior or unauthorized access attempts. Logging and auditing container activities can provide valuable insights into potential security incidents and help in identifying and mitigating any vulnerabilities. Regularly reviewing and analyzing these logs can help you stay one step ahead of potential threats.
In addition to monitoring, implementing network segmentation is another best practice for securing container orchestration platforms. By segmenting your network, you can isolate containers and limit the potential impact of a security breach. This can be achieved by using virtual private networks (VPNs) or network policies to restrict communication between containers and other network resources. Network segmentation adds an extra layer of security and minimizes the attack surface.
Another important consideration is the use of vulnerability scanning tools. These tools can help identify any known vulnerabilities in your container images or the underlying infrastructure. By regularly scanning your containers for vulnerabilities, you can proactively address any security issues before they are exploited. It is important to integrate vulnerability scanning into your continuous integration and deployment pipelines to ensure that all containers are thoroughly checked for vulnerabilities before being deployed.
Lastly, regular security assessments and penetration testing are essential for maintaining container security. By conducting periodic security assessments, you can identify any weaknesses or vulnerabilities in your container orchestration platforms. Penetration testing can simulate real-world attacks and help you understand the effectiveness of your security measures. By regularly assessing and testing your container security, you can continuously improve and strengthen your defenses.
In conclusion, securing container orchestration platforms is a critical aspect of DevOps teams’ responsibilities. By following these best practices, such as using trusted container images, implementing strong access controls, monitoring container activity, implementing network segmentation, using vulnerability scanning tools, and conducting regular security assessments and penetration testing, DevOps teams can enhance the security of their containerized environments. By prioritizing container security, DevOps teams can ensure the integrity and confidentiality of their applications and data, ultimately contributing to a more secure and resilient software development process.In conclusion, implementing container security best practices is crucial for DevOps teams to ensure the protection of their applications and data. By following these practices, such as using trusted container images, regularly updating and patching containers, implementing access controls, and monitoring container activity, teams can mitigate potential security risks and vulnerabilities. Additionally, conducting regular security audits and staying updated on the latest security threats and solutions are essential for maintaining a secure container environment. Overall, prioritizing container security is essential for DevOps teams to build and deploy applications with confidence and protect against potential security breaches.